Breach of firm's IT Systems by external parties
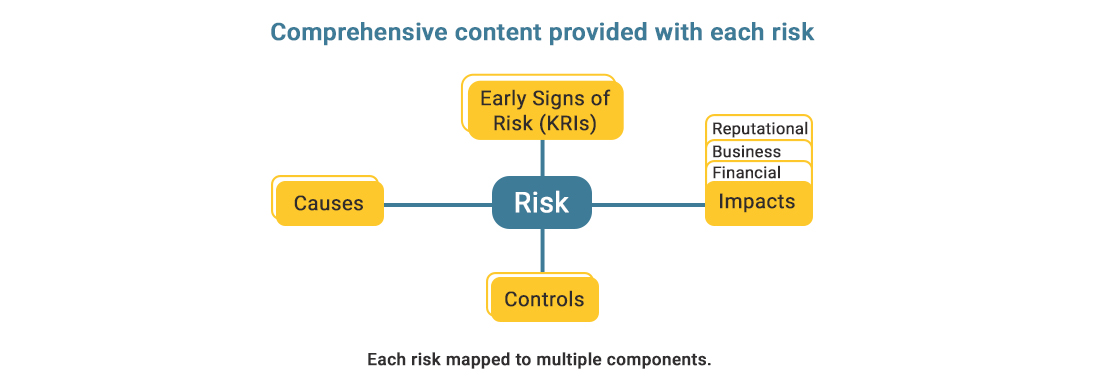
Below are the details of the operational risks covered within this selected sub-risk category:
Theft of intangible assets in digital form
Risk Description: -
Theft or robbery of intangible assets in digital form E.g.:-
- Theft of customer database by external hackers from IT Systems.
- Theft of employee database by external hackers from IT Systems.
- Theft of confidential documents by external hackers from laptop of senior managers.
Unauthorised updates to information within firm's IT Systems for fraudulent purposes
Risk Description: -
External parties may exploit weaknesses in firm's IT Systems to execute updates to information within the IT Systems, where such updates enables involved external parties to commit fraud. Examples of updates may include: -
- Update customers' email or mailing address to receive communication sent by firm to the customers.
- Update passwords for online accounts.
- Add new payment instructions to setup periodic payment from customer account into account of fraudsters.
- Create fictitious invoices, which are recorded as payable to the fraudster account.